- Saif Akhter
Concept of a cyber attack
A key component of both present and future information systems is machine learning (ML), which is already being used in a wide range of fields. Nevertheless, the application of machine learning in cybersecurity is still in its infancy, exposing a substantial gap between theory and reality. The fundamental reason for this disparity is that we need more technological advancements to determine the actual role of machine learning in cybersecurity. Until the benefits and drawbacks of machine learning are widely recognized, the technology’s full potential will never be realized. The world has witnessed a cybersecurity evolution over the past few decades. Sophisticated cyberattacks now involve phishing, malware, machine learning, and artificial intelligence.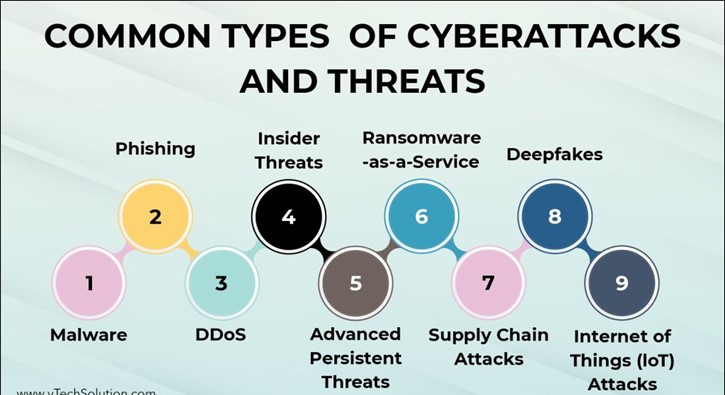
Evolution over time
Cyber dangers have changed substantially since the Internet was first used in the 1980s. One prominent early attack that led to the development of antivirus software was the “Morris” worm of 1988. Advanced malware became increasingly prevalent in the 1990s and early 2000s. One example is the “ILOVEYOU” worm, which infected millions of machines and cost $15 billion in damages in 2000. Advanced persistent threats (APTs) became the new weapon of choice for cybercriminals by the mid-2000s, as the 2010 Google “Operation Aurora” hack showed. In the 2010s, ransomware attacks gained popularity, and in 2017, the worldwide crypto worm attack known as “WannaCry” caused extensive harm. The COVID-19 pandemic in 2020 caused a spike in cyberattacks, with hackers obtaining confidential information from sites like the World Health Organization. Major corporations such as Software AG have been the targets of ransomware attacks, demonstrating the continued susceptibility of even highly resourced organizations to cybercrime.Role of AI and ML in cybersecurity
Modern techniques for identifying, evaluating, and reducing risks are being made possible by artificial intelligence (AI) and machine learning, revolutionizing cybersecurity. Large volumes of data can be analyzed in real time by AI-powered systems, which makes it possible to spot anomalies more accurately and see potential hazards before they pose a threat.
Furthermore, by identifying patterns in data that people would miss, AI can improve real-time threat identification and enable cybersecurity systems to react more quickly and efficiently.
Nevertheless, cybercriminals are turning this same technology into weapons. Cybercriminals can circumvent conventional defenses because AI and ML automate and optimize attacks.
AI and ML-based cyberattacks
Cybercriminals use machine learning in cybersecurity to create increasingly sophisticated, automated, and adaptable attack techniques.
- AI-Generated Phishing: Cybercriminals use natural language processing (NLP) models to construct phishing emails that imitate accurate communications by examining previous exchanges. By closely mimicking actual language patterns, these emails are designed to evade typical spam filters and contain dangerous links or attachments.
- Adaptive Malware: AI-driven malware that uses reinforcement learning to change its code and behavior in real-time in response to detection attempts. Polymorphic malware modifies its file signature or encryption regularly to avoid detection by signature-based antivirus software.
- Automated Social Engineering: AI creates highly customized attacks by analyzing digital footprints and social media using deep learning models. Artificial intelligence (AI)-generated spear-phishing or impersonation communications are customized to target weaknesses by anticipating user behavior.
- AI-Powered Botnets: AI optimizes the dispersion of DDoS attacks by enhancing botnet efficiency through machine learning. Swarm intelligence is used by infected devices to coordinate assaults in real-time, making them more challenging to identify and stop.
- AI-Evasion Techniques: Cybercriminals regularly test and refine malware using AI models such as generative adversarial networks (GANs), exposing flaws in security systems. AI is used by polymorphic malware to dynamically alter its code, preventing standard antivirus and intrusion detection systems from detecting it.
How advancements in 5G amplify cyber risks
Significant improvements by 5G include massive IoT scalability, ultra-low latency, and increased throughput. Even if these improvements are advantageous, they increase cybersecurity risks:
- Expanded Attack Surface: The proliferation of linked devices, such as smart sensors and driverless cars, increases the number of possible points of entry for cyberattacks. Every link and gadget has the potential to be vulnerable.
- Decentralized Networks: Multiple edge computing nodes are used in a more distributed architecture in 5G networks. Because of this decentralization, there are more attack avenues, and it is more challenging to implement uniform security measures throughout the network.
- Complex Security Challenges: The complex interactions between billions of devices, heterogeneous networks, and dynamic communication protocols make threat detection and response more difficult. Monitoring must be ongoing, and sophisticated security solutions must be flexible to secure such a large and heterogeneous ecosystem.
- Virtualization and SDNs: Added Complexity: Software-defined networks (SDN) and virtualization are major components of 5G networks, which boost network flexibility at the expense of added complexity. Vulnerabilities in virtualized settings can be used by attackers to obtain access to vital network operations.
- Exploits for Network Slicing: 5G presents the idea of network slicing, in which several virtual networks share physical infrastructure to operate. Attackers can migrate across slices or target a slice with fewer security restrictions if it is not adequately guarded.
- AI and ML-based Automated Attacks: Machine learning facilitates malware development that can change its behaviour to avoid detection. Because so many devices are linked to a 5G network, adaptive malware can take advantage of flaws in real-time and surpass conventional security measures.
- Self-Evolving Attacks: By employing machine learning in cybersecurity, attackers can create attacks that adapt to triumphs and mistakes, continuously improving their strategies. To make an assault more successful, for example, ML algorithms can assist attackers in modifying their DDoS tactics in response to the network’s reaction.
The growing sophistication of cyber threats
The growing sophistication of cyber threats is a pressing concern as technology advances. Cyber threats have now entered a new, more advanced stage of lethality.
- Evolution of Threats:
Traditional Threats: At first, cyber threats were quite simple. For example, worms and viruses that an operating system’s security could quickly identify corrupt data and systems on a device. - Role of Emerging Technologies:
AI and ML: Cybercriminals use artificial intelligence (AI) and machine learning (ML) to automate assaults, analyze data, and develop more specialized and successful phishing schemes.
5G Networking: 5G networks’ greater connectedness increases the attack surface and facilitates threats’ ability to spread swiftly across systems and devices. - Techniques and Tools:
Ransomware: Ransomware attacks have become more advanced, with attackers using encryption methods that are increasingly difficult to break.
Social Engineering: Cybercriminals use sophisticated social engineering techniques to manipulate individuals into divulging sensitive information or granting access to systems. - Defence Strategies:
Adaptive Security Measures: Organizations must have adaptable security measures to counteract changing threats. One example is using AI-driven security tools that can anticipate and lessen threats.
Regular Updates and Training: Continuous updates to security systems and regular training for employees on recognizing threats are crucial in staying ahead of cybercriminals.
The interplay between technological advancements and cybersecurity strategies
The number of networks and connected devices has increased significantly, thanks to new technologies like 5G and IoT, which increase the number of potential attack points. Attackers can automate and scale their activities using sophisticated tools and platforms. Advanced persistent threats (APTs), which may elude conventional defenses and stay undetected for longer, and multi-stage exploits are examples of sophisticated and coordinated attacks made possible by technological advancements.- AI and ML: AI and machine learning in cybersecurity are automating threat identification and execution, enabling increasingly sophisticated attacks. By automating and optimizing threat identification and execution, these technologies open the door to increasingly sophisticated attacks. While ML algorithms may find and attack vulnerabilities more quickly than conventional techniques, malware driven by AI can evolve to evade defenses.
- 5G: The attack surface is increased by 5G’s decentralized architecture and increased connectivity. Attackers can use numerous IoT devices to launch massive DDoS assaults or gain access to networks through various entry points.
- AI-Based Defenses: AI-driven systems enhance threat detection and response by analyzing large datasets for anomalies and automating real-time defenses using machine learning algorithms.
- New Security Standards for 5G and IoT: Emerging standards include advanced encryption (e.g., AES-256), secure network slicing, and enhanced authentication protocols (e.g., multi-factor authentication) to protect against breaches in 5G and IoT environments.
- Continuous Adaptation: To keep pace with technological changes, cybersecurity must constantly updates to threat models and defensive techniques, integrating new tools and methodologies to stay ahead of evolving threats.
Conclusion
As the horizons for AI and ML expand, they will continue to play a dual role in cybersecurity, serving as both formidable protection tools and catalysts for increasingly complex cyberattacks. By improving threat identification through behavior analytics, anomaly detection, and prediction algorithms and enabling real-time responses to emerging threats, machine learning is transforming cybersecurity. Cybercriminals, however, are using the same technology to construct highly targeted, intelligent threats that bypass conventional defenses, automate attacks, and modify the malware. The introduction of 5G networks has further complicated this environment by expanding the attack surface through decentralizing networks and increasing the number of connected devices. Cybersecurity tactics must keep up with these advancements by incorporating ai and ml to anticipate attacks in a more linked digital environment and defend against increasingly adaptive ones. Organizations must fully utilize machine learning to create predictive security measures and robust methods to fend off increasingly complex assaults if they want to stay ahead of the curve. It’s an ongoing struggle, but we can fortify our defenses and remain one step ahead of new threats if we invest appropriately in AI and ML. Moving forward—these developments will open the door to a future with more security!
Saif Akhter
Saif is the Data Engineer at TenX
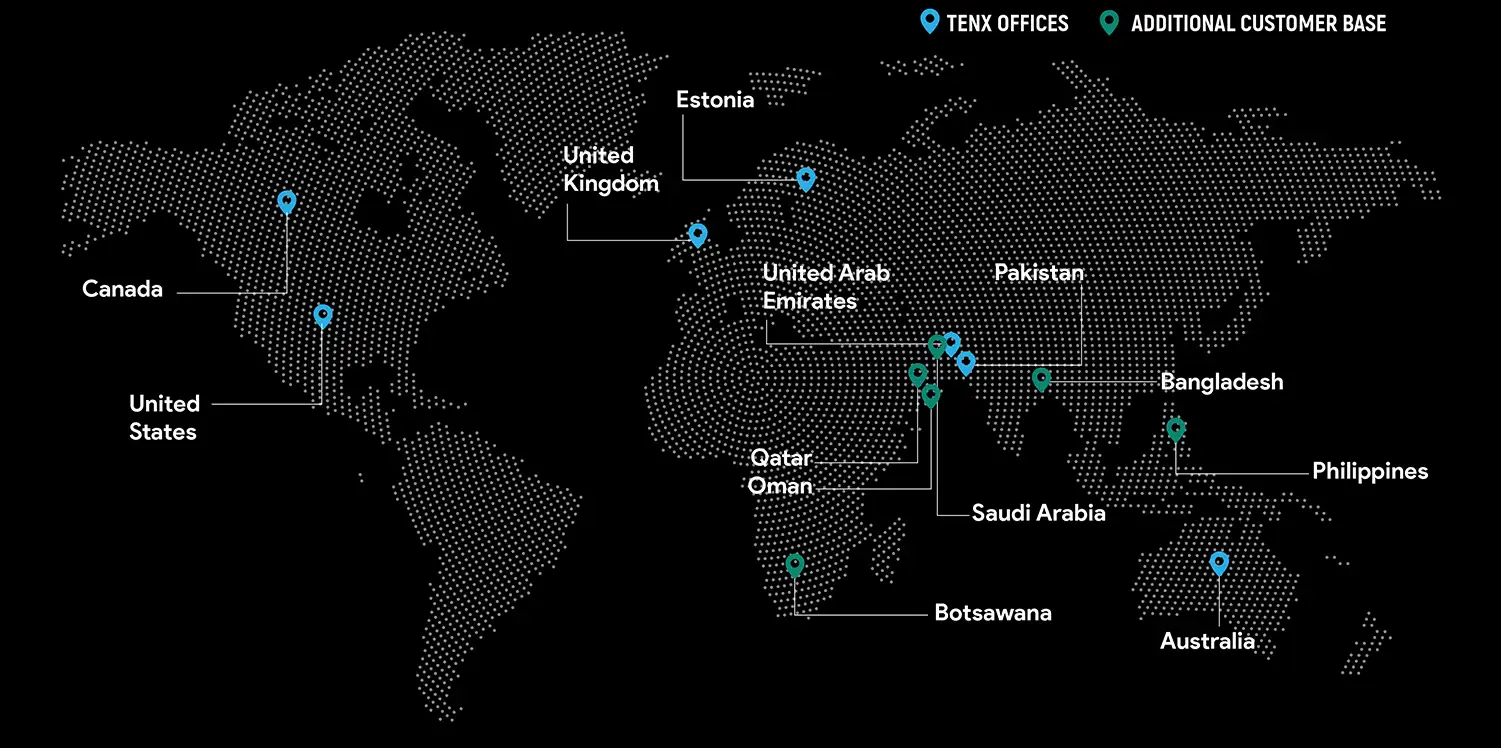
Global Presence
TenX drives innovation with AI consulting, blending data analytics, software engineering, and cloud services.
Ready to discuss your project?